In An Identity Management System What Is The Function Of The Authoritative Source
In an identity management system what is the function of the authoritative source. Data identity and key management modernization is being shaped by. Specify the owner of a data item. Obtain the current password for a user through the psync system.
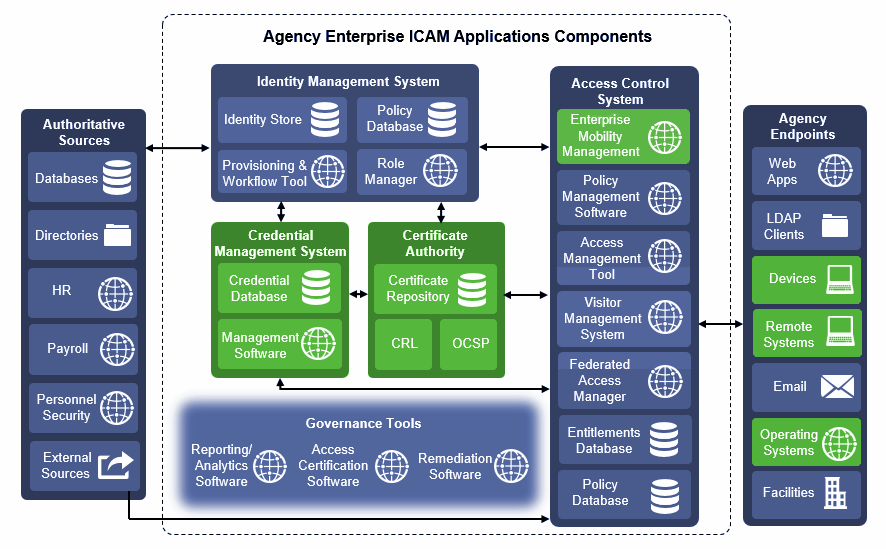
IAM Framework IAM comprises of two modules namely access management module and identity management module. If the question is not here find it in Questions Bank. MIM looks at the state of attributes in the source identity store the value of each attribute and whether it has changed and synchronizes those attributes with the systems and apps it is connected to.
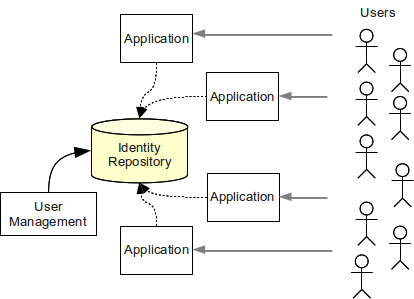
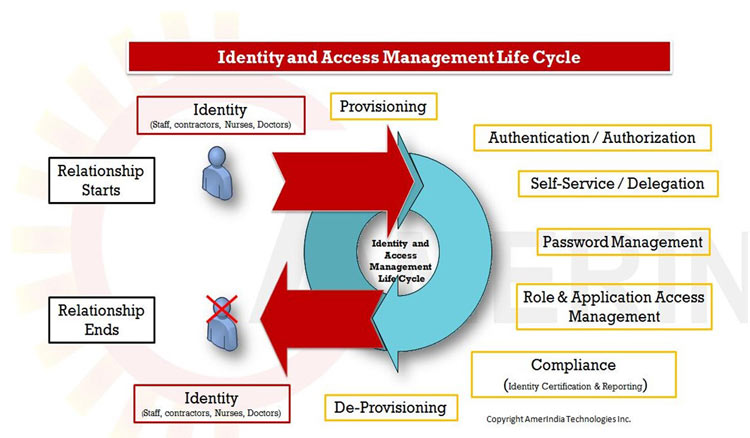
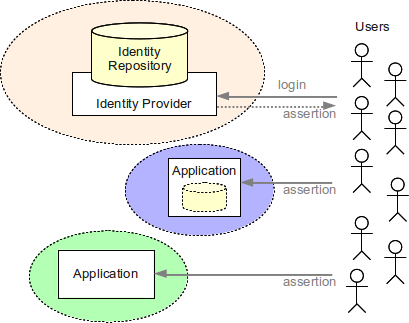
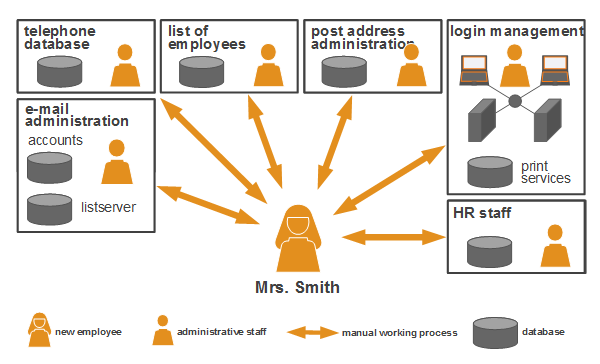
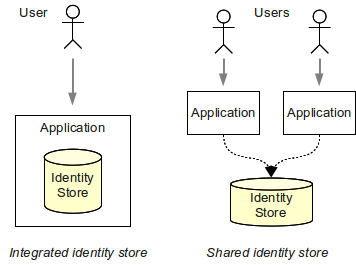
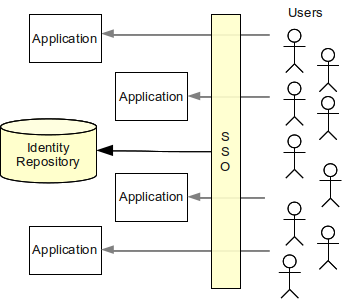
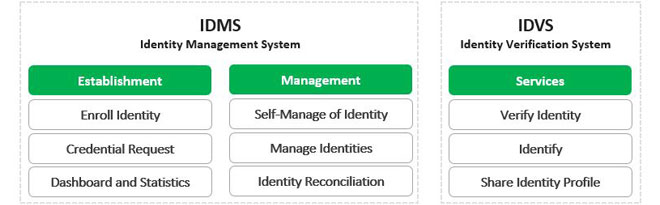
Leverage your professional network and get hired. This is the Identity side of IAM and ensures that every user is who they say they are. Authoritative source or Identity store is the source of the data that flow down to the Identity Management System.
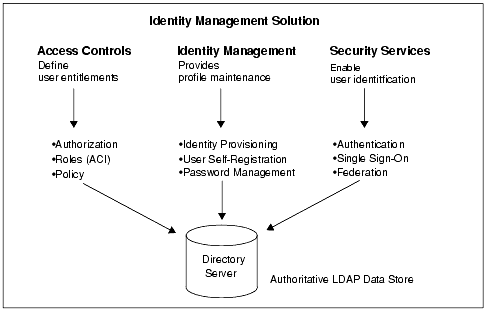
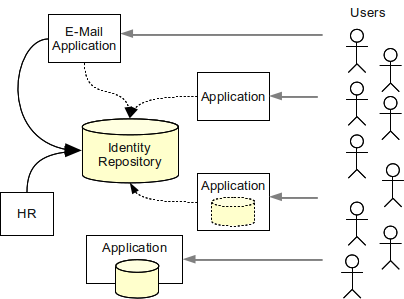
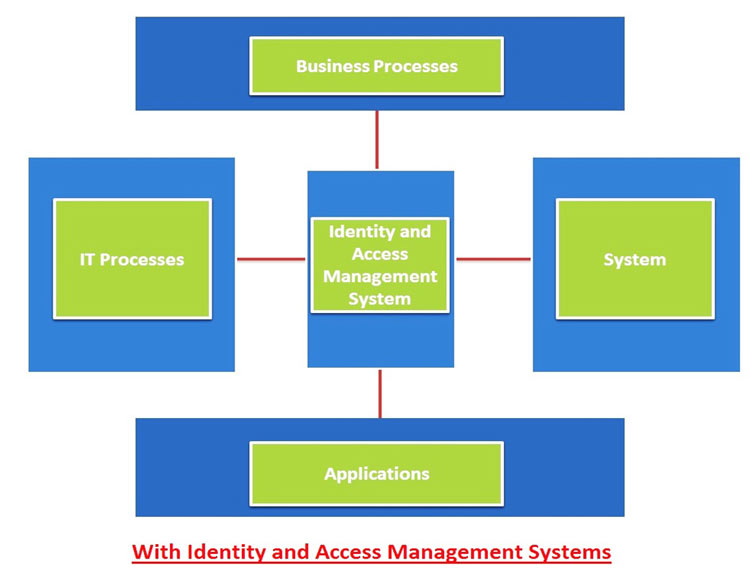
Identity Management IAM is a generic term used to describe an organizations internal processes that focus on managing user accounts and corporate network resources including access rights for organizations users applications and systems. A managed repository of valid or trusted data that is recognized by an appropriate set of governance entities and supports the governance entitys business environment. An authoritative source or identity store is simply a directory or database that contains peoples identity detail.
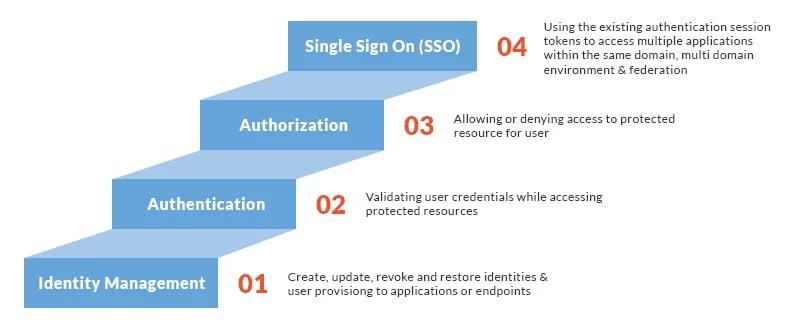
Its external to Google and therefore referred to as an external authoritative source. We will discuss the following major IAM functions that are essential for successful and effective management of identities in the cloud. Identity management ID management - or identity and access management IAM - is the organizational and technical processes for first registering and authorizing access rights in the configuration phase and then in the operation phase for identifying authenticating and controlling individuals or groups of people to have access to applications systems or networks based on previously authorized access rights.
Identity controls are emerging as a primary security perimeter for cloud applications. Cryptography and Endpoint Protection Group Exam Answers September 9 2020 Last Updated. It provides identity management functions such as controlling user access to organizational secure systems and ensures that all users and services are properly authenticated authorized and audited.
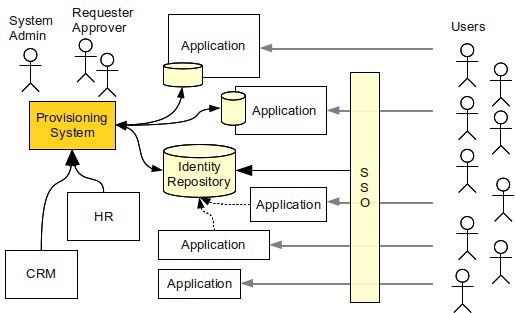
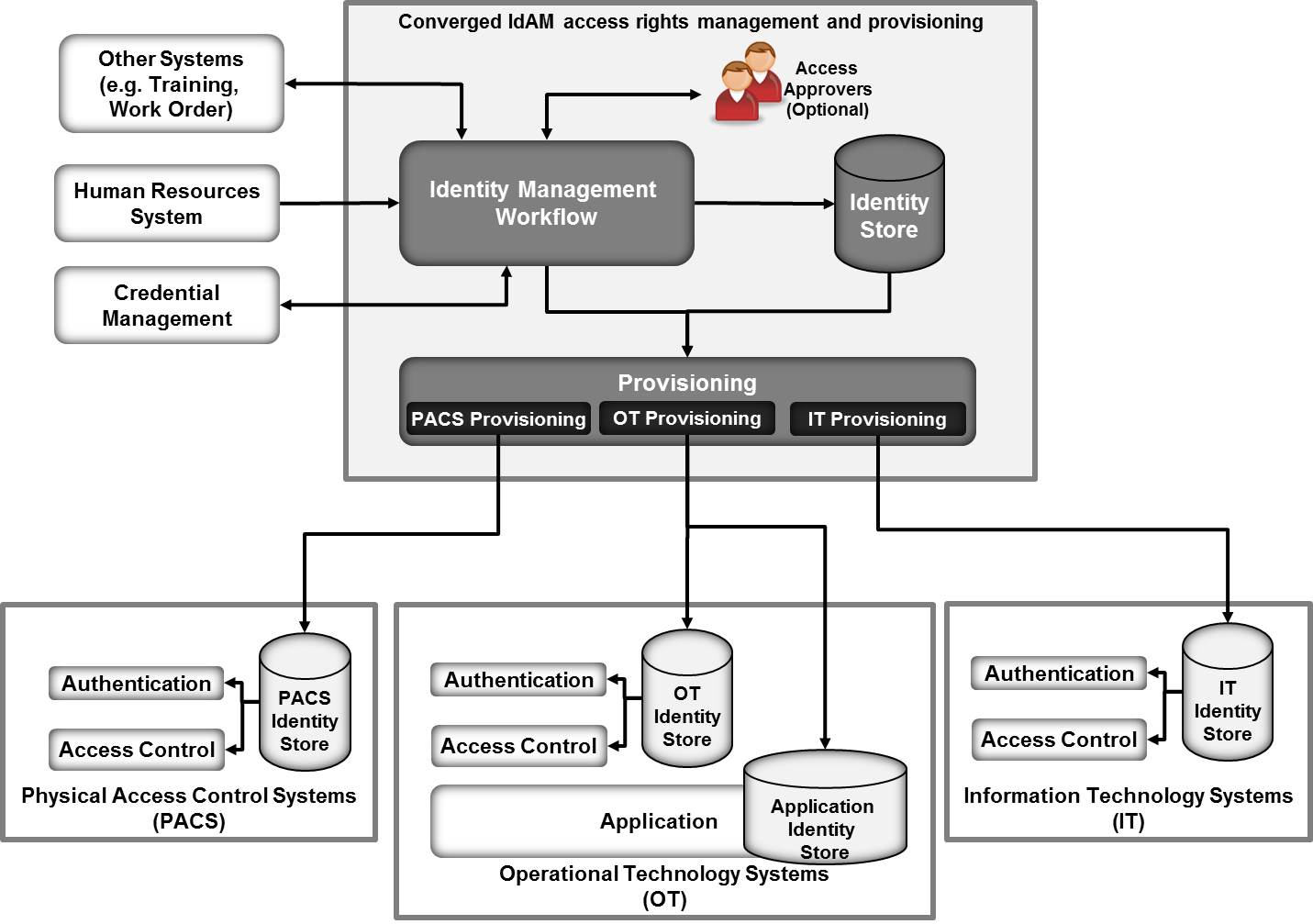
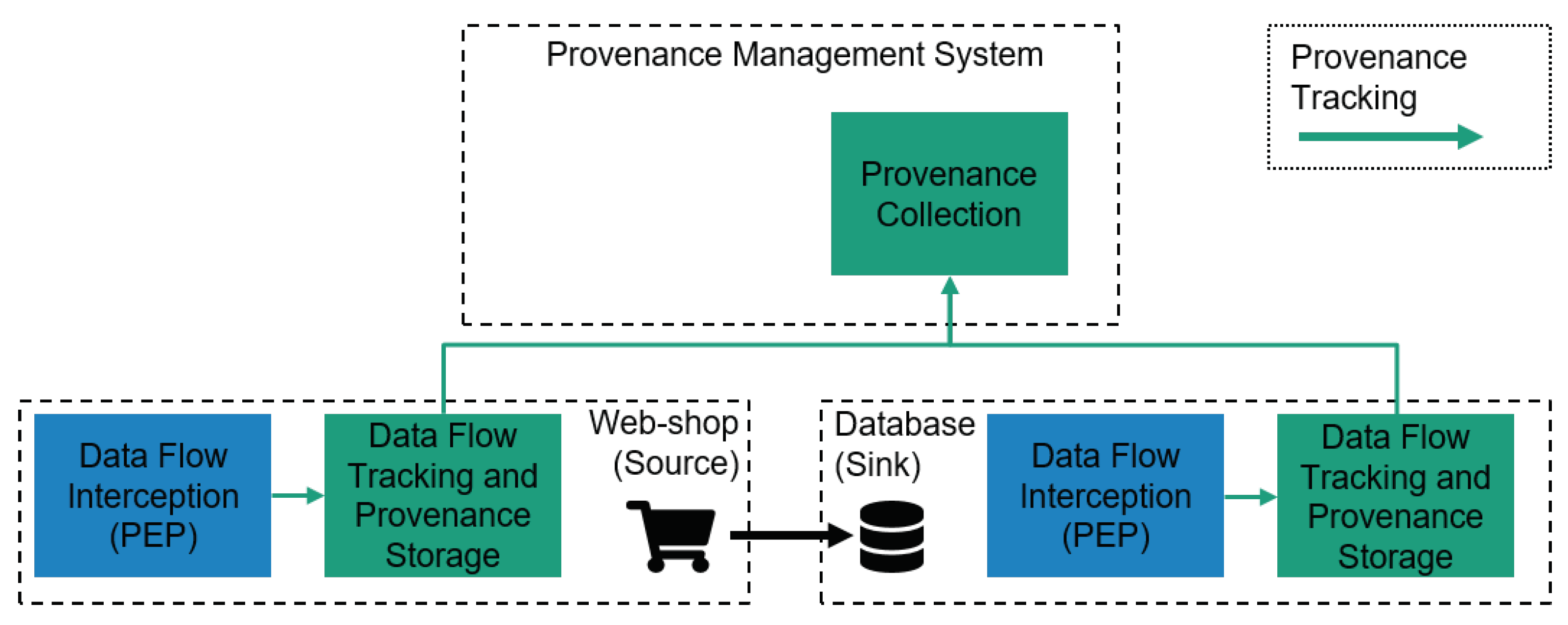
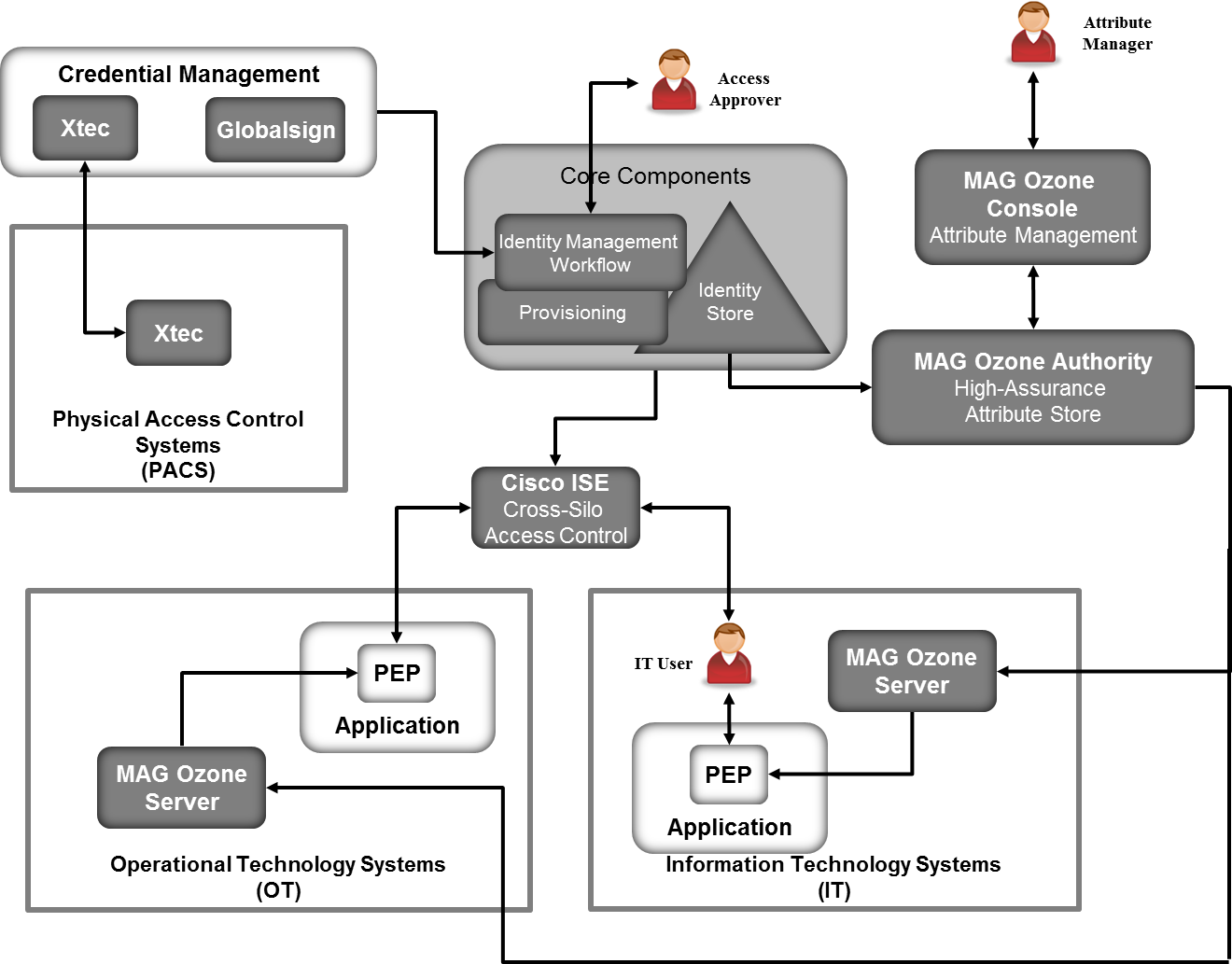
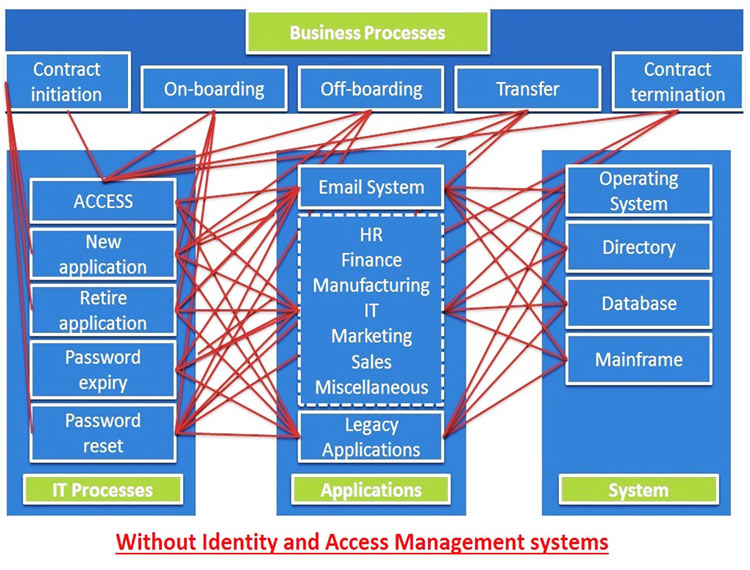
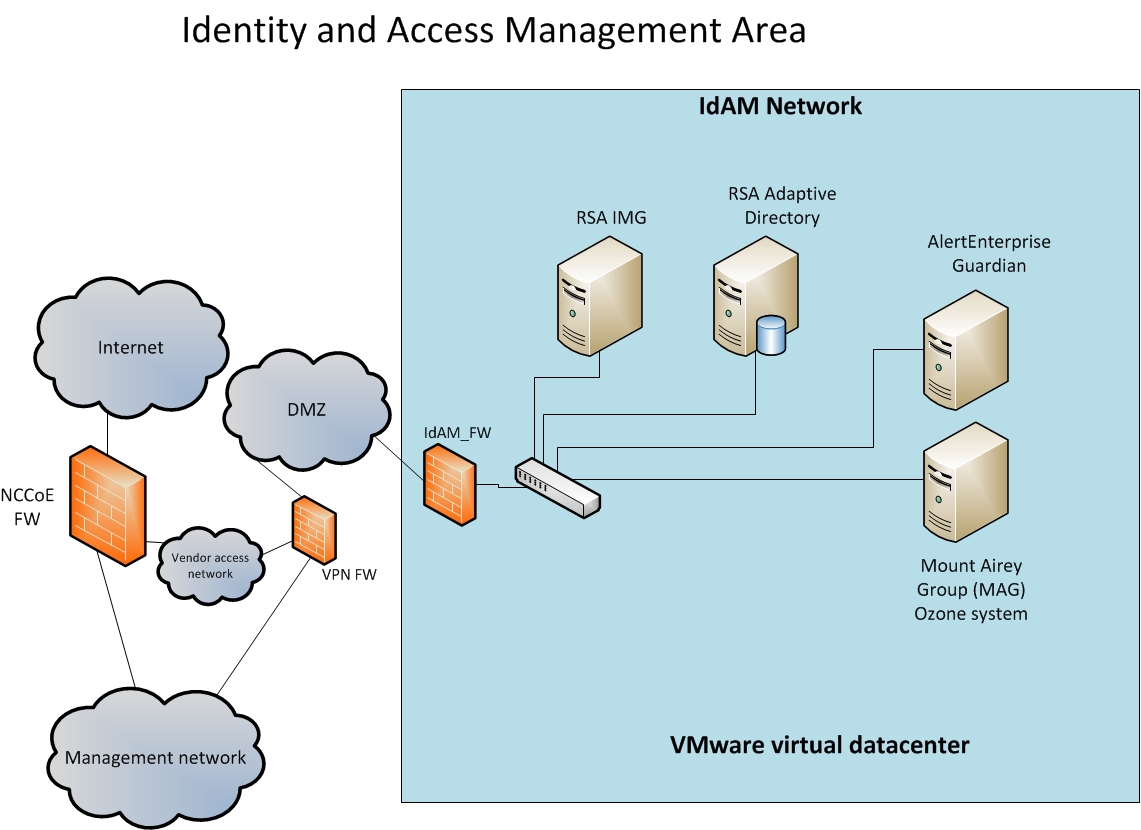
An authoritative source of identity is provided by managing and controlling authentications to multiple systems via a centralized IAM irrespective of the method used as shown in Figure 124. Modules 21 23.
We will discuss the following major IAM functions that are essential for successful and effective management of identities in the cloud.
Readiness to conduct cloud-based Identity and Access Management IAM as well as understanding the capabilities of the organizations cloud computing providers. Identity controls are emerging as a primary security perimeter for cloud applications. MIM at its core was designed as an identity and access management framework for Azure and Windows Server Active Directory to help control other systems as well. Modules 21 23. Authoritative source or Identity store is the source of the data that flow down to the Identity Management System. Additional terms are used synonymously with identity-management system include. Press Ctrl F in the browser and fill in whatever wording is in the question to find that questionanswer. Coordinate the management of user identity across system boundaries. A managed repository of valid or trusted data that is recognized by an appropriate set of governance entities and supports the governance entitys business environment.
Identity Management IAM is a generic term used to describe an organizations internal processes that focus on managing user accounts and corporate network resources including access rights for organizations users applications and systems. A managed repository of valid or trusted data that is recognized by an appropriate set of governance entities and supports the governance entitys business environment. Data identity and key management modernization is being shaped by. From the external authoritative source user accounts and groups can be automatically provisioned to Cloud Identity or Google Workspace. The authoritative source for identities is the sole system that you use to create manage and delete identities for your employees. In most cases it is the human resources system which provide business role new hire termination job change and other information relevant to RBAC management. Identity management otherwise known as identity and access management IAM is an identity security framework that works to authenticate and authorize user access to resources such as applications data systems and cloud platforms.

























Post a Comment for "In An Identity Management System What Is The Function Of The Authoritative Source"